Manage Security Roles
Each Meridian vault can have any number of security roles, but the fewer there are, the easier they are to manage and assign.
To manage security roles:
-
In Configurator, on the Vault menu, select Roles and Privileges.
The Roles and Privileges dialog box appears showing the current security roles that have been configured, if any.
-
To view the privileges for custom objects in the vault such as navigation views, reports, lookup lists, document types (if document type security is enabled), and so on, select the Show object privileges check box in the lower-left corner of the window.
The custom object names appear in blue text.
Note:
-
When the Use document type security option is enabled for a vault , the Document privileges group that would otherwise apply to all document types is removed from the Privileges column. The privileges for each document type can then be found below the name of each document type in the Document Types group.
-
Custom command names do not appear in the list until after their Can Execute privilege has been created by clicking the Privileges button at least once as described in Create And Edit Custom Commands.
-
Follow the appropriate procedures below.
-
Changes to existing roles take effect immediately. New roles must be assigned to vault folders as described in Assign Security Roles to a Folder.
-
By default, new vaults have no security roles assigned and the first role that is assigned is granted exclusive access to the vault until other security roles are assigned. Create the role with the highest level of access first (for example, Administrator) and assign the system's administrators to it at the root of the vault before assigning any other security roles. This will prevent you from accidentally denying System Administrators access to the vault and assigning other roles. It will also grant System Administrators access to the entire vault unless role inheritance is overridden by assignments at any folders.
Important!
Before configuring security, be sure to create a rescue account to ensure you do not accidentally deny access to all System Administrators.
-
By default, folders inherit their security role assignments from their parent folder recursively all the way to the root of the vault. This makes setting security for the entire vault as easy as assigning roles just once at the root of the vault.
Role assignments for specific folders may then be overridden, if necessary, as described in Assign Security Roles to a Folder.
-
After configuring and testing the roles in a vault, create a Windows user group for each role. The groups should be domain or local groups, as described in Meridian Support For Microsoft Active Directory. Then, assign the Windows user groups to roles in the vault. You may then easily add new users to the system by simply assigning them to the correct Windows user group without the need to change the role assignments in the vault.
-
To export, import, or clear the security role assignments of a folder and its sub-folders, see Assign Security Roles to a Folder.
Note:
If a user is a member of multiple roles assigned to the same folder, their effective rights in that folder are those of the more permissive role. Therefore, avoid assigning users to multiple groups that are assigned to roles applied to the same folders.
Configure the role with the most privileges first, and then copy the privileges of that role to the next role. Clear unnecessary privileges from the new role. Repeat copying the privileges of the role and clearing privileges until all roles have been created.
To create a role:
-
Click the New Role button.
The New Role dialog box appears.
-
Click options or type values using the descriptions in the table below.
-
Click OK.
A new column is added to the Roles and Privileges window with the copied privileges.
-
Select or clear the check box in the Privileges column for that role.
For information about each privilege, see Security Privilege Descriptions.
Note:
Privileges for tables created prior to Meridian 2010 are not available until after they have been created by clicking the Privileges button on the General tab of the table in Configurator.
- When you are finished creating roles, click OK.
To edit a role:
-
Select or clear the check boxes in the Privileges column for the role.
For information about each privilege, see Security Privilege Descriptions.
Refer to the cursors in the below figure when reading the following instructions to quickly select or deselect groups of privileges or roles.
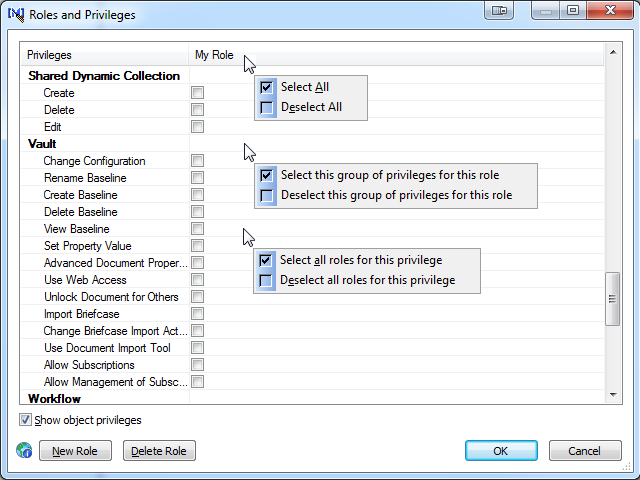
-
Choose one of the following options:
-
To select or deselect all privileges for a role:
-
Right-click the role name.
-
Click Select All or Remove All.
-
To select or deselect all privileges in a group for single role:
-
Right-click the empty cell at the intersection of the privilege group name row and the role column.
-
Click Select this group of privileges for this role or Deselect this group of privileges for this role.
-
To select or deselect all roles for a single privilege:
-
Right-click the name of a privilege.
-
Click Select all roles for this privilege or Deselect all roles for this privilege.
-
Click OK.
To delete a role:
-
Click the Delete Role button.
The Delete Role dialog box appears.
-
Select the role that you want to delete.
-
Click OK.
The role is deleted.
Security role options
|
Display Name
|
Type the name of the role as you want it to appear to users. This name should reflect the functional role of the user with respect to documents. Example names are Administrator, Manager, Author, Reviewer, and Viewer.
|
|
Name
|
A default internal name is calculated. Accept the default in most cases.
|
|
Copy privileges from
|
Select an existing role from the list that has privileges equal to or greater than the new role. This will make editing the privileges of the new role easier if you simply delete the privileges that do not apply to the new role.
|

